22 Feb Cyber Ransomware
[mashshare]
Cerber Ransomware that Talks
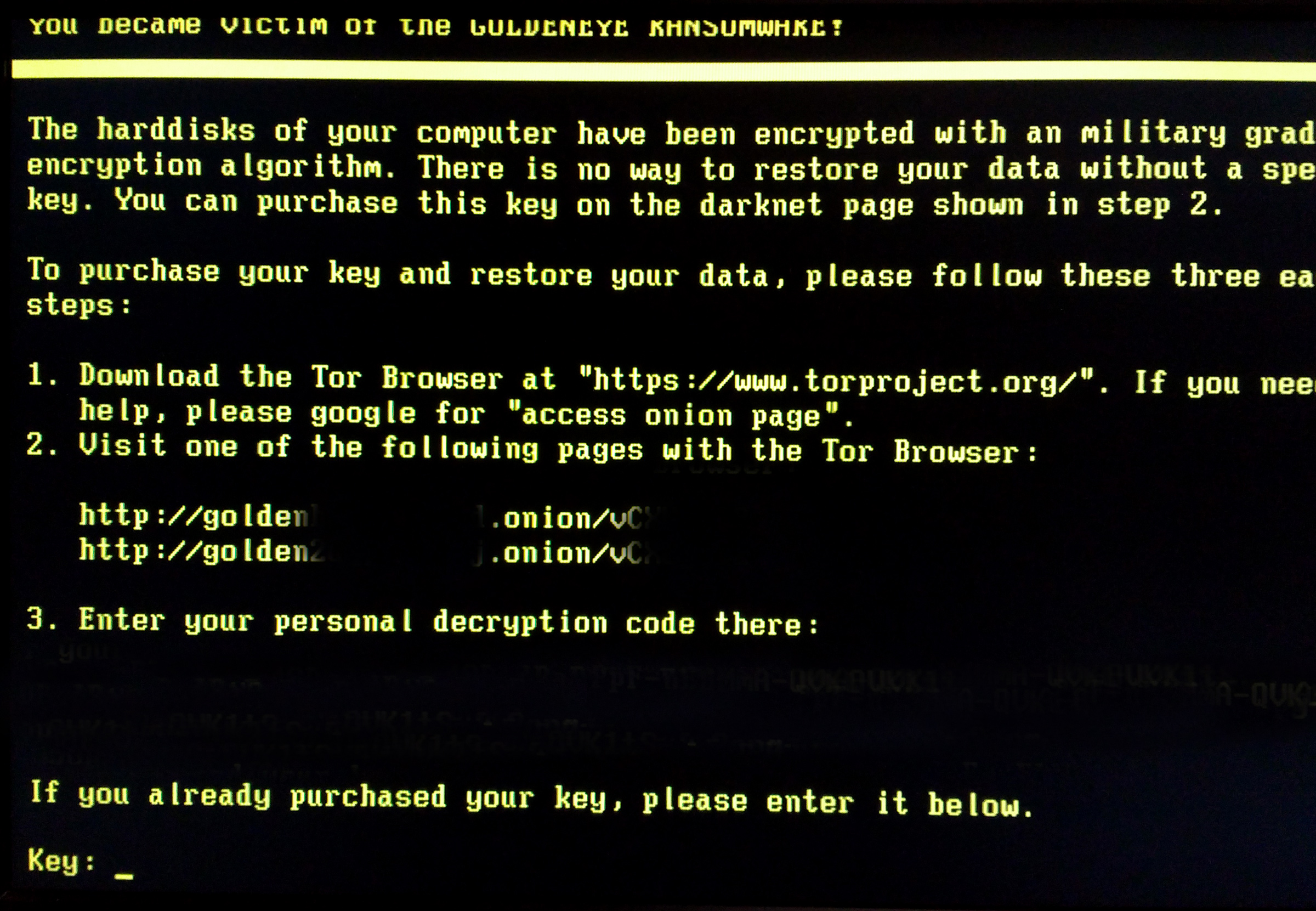
“Attention! Attention! Attention! Your documents, photos, databases and other important files have been encrypted!” When you hear these words from your computer, you’re in trouble. A kind of malware called Cerber ransomware has hit the machine, and it’s done just what it says: It’s changed files on your computer into encrypted form, making them useless until you give the perpetrator money to restore them.
Cerber is ransomware. If it hits your computer and you don’t have a safe backup, you have the choice of giving a criminal money or losing important files. You have to make the payment by Bitcoin, an anonymous form of online payment. The dollar cost varies with the Bitcoin exchange rate; currently it’s around $1200. To pay, you have to log into a website and follow the instructions.
Cerber operates in a perversely businesslike way.
Its creators offer it as RaaS (Ransomware as a Service). Small-time criminals rent its use to launch attacks on people’s computers. This means that people with hardly any technical knowledge can use it to steal money. It’s strange to think of racketeers having a trustworthy reputation, especially when no one knows who they are, but that’s how it works.
It’s been around for about a year and has gone through multiple versions. It even tells you which version has hit you, which can be a clue for how to get rid of it. Ways to get back your files with older versions may not work with newer versions. Cerber ransomware only affects Windows systems. It doesn’t hit computers that appear to be in Russia or neighboring countries, which could be a clue to where the perpetrators are from.
A recent wave of attacks takes advantage of bugs in older system software versions. The perpetrators trick people into navigating to their websites, or they deposit a malicious script into a legitimate site. Just opening the page will deposit and launch a downloader on the victim’s computer. The downloader will install and run the Cerber code. Old versions of Adobe Flash, Internet Explorer, Edge, and Silverlight can leave a computer vulnerable.
If Cerber hits
As mentioned earlier, Cerber ransomware announces itself with a spoken message as well as a window making demands. The tone is matter-of-fact, telling you what to do. One of its statements, though, is a lie: “Any attempts to restore your files with third-party software will be fatal for your files!”
What is true is that you have to get rid of the ransomware before restoring the files. You also have to make sure you have a good backup; Cerber ransomware is thorough about attacking any copies it can find. It goes after mapped drives, network shares, and shadow volume copies. Your best safety from Cerber, and from ransomware in general, is an offsite cloud backup.
The first step is to shut down the computer. That will keep Cerber from doing any more damage than it’s already done. Adtech IT Solutions can help you get rid of ransomware safely. Be sure to take the computer off the network before attempting any recovery procedures.
Prevention and protection
Ransomware is a widespread threat. Some victims have paid thousands of dollars to get their files back. Not everyone who pays recovers their files; you’re dealing with crooks, after all. An offsite cloud backup is essential protection. It should update as often as your network capacity can manage. If you lose only the last hour’s files, you can absorb the loss.
Keeping browsers and system software up to date with all security patches is important. Cerber relies on bugs in old software to attack computers. Having up-to-date security software on the computer will prevent many attacks. Be careful of any unfamiliar websites you visit, and don’t click links in suspicious-looking email. If your browser warns you that a site may be dangerous, stop right there.
With some kinds of ransomware, you can recover your files even if you don’t have a backup. Don’t panic, but check with us. Paying criminals only encourages them to attack you again. There are usually ways to get your files working again without giving in.